Spain plans to fine large firms that fail to notify authorities of cyberattacks
Draft law would allow government agencies to monitor the security of companies’ computer systems


The Spanish government plans to penalize companies that provide essential services, such as electricity and transportation, as well as digital service providers if they fail to promptly notify authorities of major cyberattacks.
Action will also be taken if companies do not take appropriate measures to avoid these kinds of attacks. The sanctions are said to be “effective, proportionate and dissuasive.” This is according to a draft law proposed by the Spanish government that aims to bring the country in line with the European Union’s Directive on the security of network and information systems (NIS Directive).
Although the effects on Spain from 2017 cyberattacks were limited, they exposed the need to have legal standards for dealing with these issues
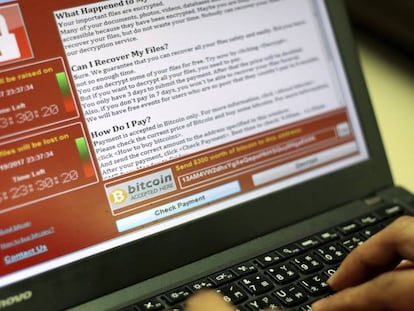
Earlier this year, on May 12 and June 27, massive global cyberattacks occurred as the WannaCry and Petya viruses hit networks worldwide. Hundreds of thousands of computers were hijacked with users hit with random demands to reactivate their computers. This revealed the vulnerability of the information networks on which our increasingly technologically advanced society depends on.
Although the effects on Spain from both cyberattacks were reported to be limited, they exposed the need to have legal standards for dealing with these issues. The government now wants to guarantee that these companies are taking adequate measures to protect their systems from hackers, or are at least resilient enough to guarantee the continuation of the services they provide to customers in the event of another similar situation.
In the case of the WannaCry attack, Microsoft distributed the security update that protected against this ransomware on March 14, but many companies had not yet installed the patch.
Three national authorities and a single point of contact
The European Union’s NIS Directive requires the creation of a single point of contact for coordination and cooperation with the European Union. In Spain, the contact will probably be the National Cyber Security Council, with the Department of National Security as the permanent secretary. Currently, the office of cybernetic coordination of the Interior Ministry manages this function.
The administration has given up on creating a single “national authority” to supervise and impose sanctions on companies. The Ministry of the Presidency will have authority over the networks of the administration; the Ministry of the Interior will manage essential service providers; and the Ministry of Energy, Tourism and the Digital Agenda will manage digital services. The Cyber Security Incident Response Teams (CSIRT), responsible for managing cyberattacks, will be integrated into the European network.
The government is already working on a legal instrument which would give it the power to monitor the IT systems of these companies that provide essential services. It would also be able to enforce preventative measures and impose punishments if companies do not apply those measures or fail to notify them of significant cyberattacks.
This law requires the coordination Department of National Security (DNS), the Interior Ministry, the National Intelligence Center (CNI), and the secretary of state for the information society and the digital agenda. The goal is to incorporate the European Parliament’s NIS directive, which mandates that member countries adopt these practices before next May.
The NIS directive requires that countries provide a list to the European Commission of essential service operators and public service providers, both public and private. The directive defines these essential sectors as: energy (electricity, oil, and gas), transportation (air, sea, and railroad), sanitation, drinking water, and digital infrastructure.
Under the draft Spanish law, the administration will have the ability to carry out audits of these companies’ security systems and impose “binding instructions” to remedy any deficiencies discovered and subsequently monitor the systems to ensure that security requirements are met.
Both types of companies – essential and digital service providers – will be obliged to communicate “incidents with significant disruptive effect” to the appropriate authorities as soon as possible. This would be a situation where there is a disruption in continued service.
The severity of cyberattacks depends on a number of factors including the number of users affected, the dependence on the affected service by other sectors, its market share, the impact of the incident, its duration, and its geographic extent. Spanish authorities will report incidents to the other EU member countries that could also be affected. This information will be confidential, but authorities can inform the public “when social awareness is necessary to avoid an incident, or to manage an already existing incident.”
The proposed law needs to specify the sanctions that will be imposed on the companies that do not comply with the law’s requirements regarding cyberattacks. The NIS directive only requires that they be “effective, proportionate, and dissuasive.” Sources for the government stated that the sanctions will be scaled, depending on the impact of the security incident or the level of non-compliance, but added they did not want to specify what those sanctions would be on the grounds that discussions on the law has not yet been completed.
Given the international nature of digital service providers, such as search engines, the directive will require that these companies appoint a representative in an EU country under the jurisdiction of which they will fall.
Two global cyberattacks
The WannaCry virus affected more than 350,000 operators from 180 countries. The cyberattack began on May 12 in the United Kingdom, where 16 hospitals were affected. In Spain, Telefónica, among other companies, was another victim of the attack. In France, the automotive company Renault had to cease production in several factories due to the virus.
On June 27, the Petya virus (a variant of the malware also known by this name) began to spread, in a more dangerous and sophisticated way compared than WannaCry. The affected companies in Spain were Maersk (logistics), DLA Piper (lawyers), Mondelez (food industry), and Saint-Gobain (construction). The Central Bank of Ukraine and the Russian oil company Rosneft were also victims.
English version by Debora Almeida.